AI solutions
What we do
Services
Experts in
How we work
If you have worked on custom software projects, you have probably noticed that about 90% of the risks that threaten software delivery recur from project to project. Different teams, different industries, different tech stacks, yet the same problems keep recurring.
As a company that provides digital product development services, after 10+ years on the market and 200+ delivered projects, we have seen this firsthand and built a structured risk management approach to spot early warning signs before they turn into missed deadlines or budget overruns. This is how we consistently achieve a 99.89% acceptance rate and keep CPI and SPI variance below 10%.
In this article, we will cover:
Before we explore software development risks, we need to define what a risk is.
The Project Management Body of Knowledge (PMBOK), a globally recognized guide that our project managers use to plan, execute, monitor, and control projects consistently and effectively, describes a risk as:
An uncertain event or condition that, if it occurs, has a positive or negative effect on a project’s objective.
At Clockwise, we categorize software development risks into organizational and technical ones. Let's see what risks are included in each category and how we manage them.
By organizational risks, we mean challenges that come from how you organize and manage the software development workflow. As we worked on various projects across different teams and collaboration models (dedicated software development team, outstaffing, etc.), we often faced the following risks.
Requirements are the backbone of any software development project. They define what needs to be built, guide design and development decisions, shape testing, and influence long-term maintenance. When requirements are unclear or poorly structured, risks multiply quickly.
Here in the table, you can see the most common requirements-related risks we have seen in our projects and the consequences they can cause:
| Risk | Consequences |
| Multiple requests combined into a single requirement | Reduced clarity and prioritization, misunderstandings during development, inaccurate estimates, rework, and delays |
| Poorly structured or inappropriate requirement descriptions (i.e., pseudo-code or references to external documents) | Misinterpretation, increased onboarding time, and inconsistent implementation |
| Strong dependency between requirements | Higher sensitivity to changes, cascading scope changes, and increased complexity in planning and delivery |
| Notes and assumptions are embedded instead of explicit requirements | Development of incorrect or incomplete functionality, missed expectations |
| Unfeasible, unclear, or untestable requirements | Implementation difficulties, inability to validate results, and increased defect rates |
| Failure to update requirements when priorities or goals change | Schedule delays, conflicting priorities, and disruption of sprint planning |
To manage these risks effectively, we document requirements in an app requirements document. It helps us:
At Clockwise, we create an app requirements document during the project discovery phase. This is the pre-development stage where we research the problem space, align on business goals, and collect all required documentation.
By investing in a well-prepared app requirements document early on, we ensure that requirements align with business needs, follow a clear structure, and describe each goal in enough detail to support predictable development. This approach helps our clients avoid $30,000+ additional spending on mid-project pivots and keep CPI/SPI variance below 10%.
According to the triple constraint theory introduced by the Project Management Institute, every software project is shaped by three tightly connected factors:
When one of them changes, the other two are affected as well.
In practice, this means limited timelines often force teams to reduce scope, while budget restrictions can slow development and push delivery dates further out. Ignoring this relationship leads to missed deadlines, rushed releases, or products that fail to meet business goals.
That is why we take a deliberate approach to balancing timeline, budget, and scope, enabling informed trade-offs instead of reactive fixes. Here’s how to manage these risks and keep development moving in the right direction.
As our experience shows, defining the scope is hard because most product owners start with a full vision. A long feature list, lots of “nice-to-haves,” and a mental picture of the final product. The problem is that development needs something more concrete than a vision: a clear, agreed set of features with boundaries, priorities, and acceptance criteria.
Common scope risks look like this:
Remember the discovery phase we mentioned earlier? That's where we reduce these risks as well - by turning "what you want" into “what we will build first,” with documentation that the development team can actually execute:
Timeline risks usually come from uncertainty. If the scope is unclear, dependencies are unknown, or integration complexity is underestimated, delivery dates become indistinct as well.
Typical time risks include:
During discovery, we focus on replacing speculation with a plan that holds up in real execution:
Budget overruns rarely come from one big mistake. As usual, they come from many small ones: unclear scope, underestimated complexity, rework, and late surprises.
Common cost risks include:
This is how discovery helps keep budget decisions grounded and transparent:
Let’s now take a look at how we managed scope, timeline, and budget risks for Creador, a marketplace for photo and video makers. The client came to us with an ambitious vision, but limited time and clear budget boundaries. Our goal was to turn a broad idea into a plan that the team could execute without constant rework or budget overruns.
Scope. We began with discovery and scope clarification. Together with the client, we broke down the full vision into a structured WBS and defined the scope of the first release.
Timeline. With the scope validated, we translated it into a concrete development plan. By splitting the product into estimable modules, we exposed dependencies early and set milestones based on verified requirements rather than assumptions. This made delivery dates predictable and achievable.
Budget. Once the scope and timeline were aligned, we prepared estimates tied directly to the WBS and detailed feature specifications. When priorities shifted, the cost impact was immediately clear, allowing our client to make informed trade-offs rather than face surprise overruns.
By anchoring decisions in discovery outputs and early validation, we reduced the initial estimate from 1,200 hours to a focused 400-hour scope, keeping cost, timeline, and scope in balance.
In some cases, we have to collaborate with our clients’ teams or engage external specialists. This occurs when the project requires highly specialized expertise (like, for example, a highly-specific framework for an AI product), such as in data engineering or niche frameworks.
From our experience, the main risks appear when external contributors are treated as detached executors rather than accountable partners. The most common issues we see include:
| Risk | Consequences |
| Poor involvement and shallow context | Misalignment with business goals and user needs, work that meets specifications but misses intent, increased rework, slower iterations, and quality gaps |
| Partners with limited industry or technology experience | Underestimated complexity, missed deadlines, unstable or fragile solutions, reactive firefighting instead of predictable delivery |
| Security and confidentiality | Exposure of sensitive data or intellectual property, increased compliance and legal risks, and growing security vulnerabilities as the project scales |
When we work with external expertise ourselves, we follow the following rules:
Stakeholders are people directly interested in the project’s positive outcome. In our projects, stakeholders are represented by a product owner and product leaders who participate directly in discussions and decision-making.
Problems start when involvement is either too low or poorly organized. Here are the risks associated with stakeholders’ involvement and project control:
| Risk | Consequences |
| Low stakeholders’ involvement | Underestimated complexity, misunderstandings around scope, increased rework, and missed expectations |
| Weak or inconsistent communication | Confusion within the team, stalled progress, and extended delivery timelines |
| Micromanagement | Reduced team autonomy and motivation, lower productivity, and diminished overall outcomes |
| Late or unclear ownership | Repeated discussions, incorrect decisions, increased friction, and higher delivery costs |
To manage stakeholder involvement, we rely on a RACI matrix. This document helps us clearly define and communicate roles and responsibilities for each task throughout the project. The matrix includes 4 roles:
Here is an illustration of how a typical RACI matrix can look in a software development project:
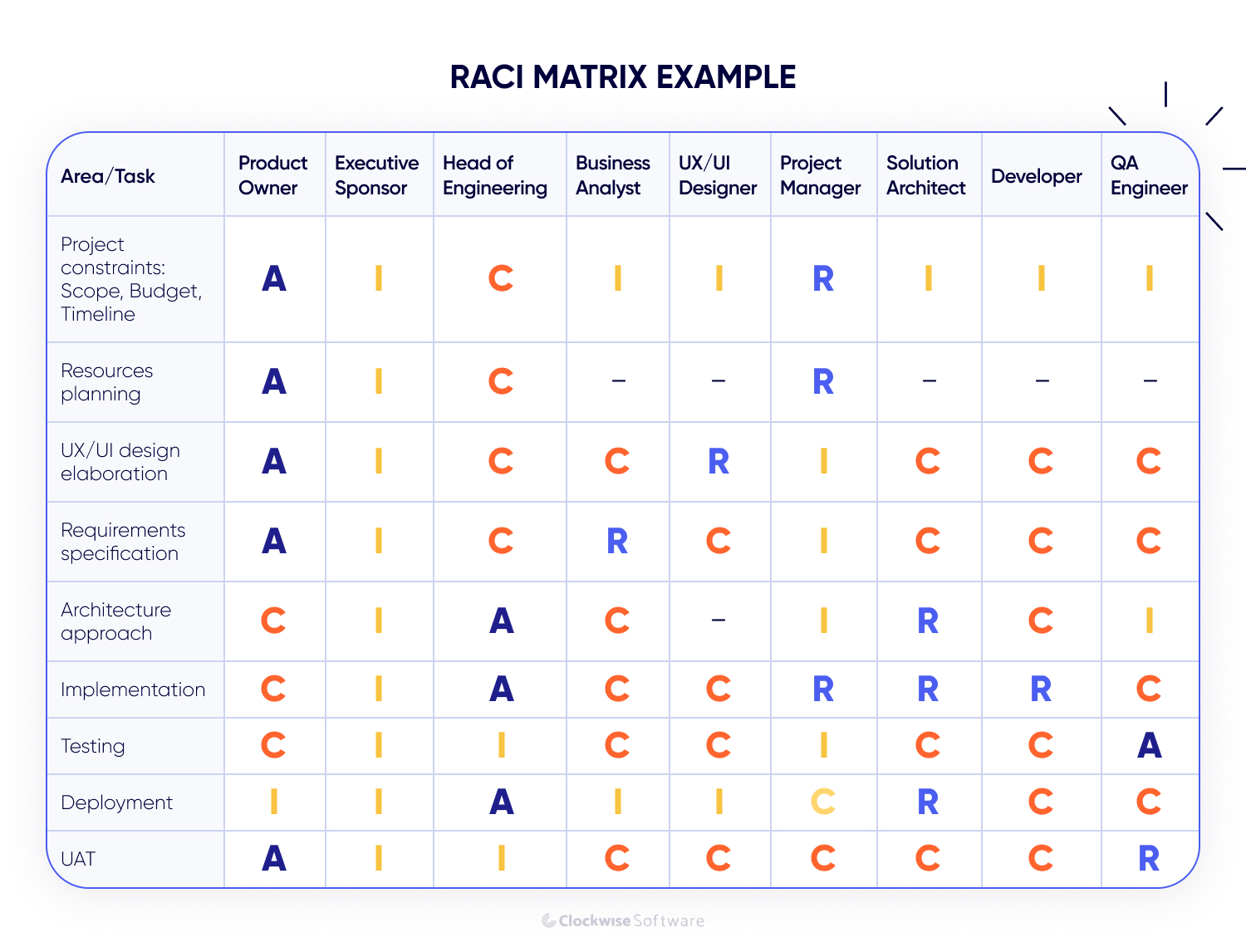
This approach makes decision ownership explicit, reduces unauthorized changes, and minimizes rework.
In our experience, involving stakeholders from the outset is essential, but we also avoid excessive meetings. Daily involvement is rarely necessary. Regular weekly or biweekly check-ins are sufficient to align on the vision, review progress, and adjust priorities without slowing the team.

Large organizational changes can significantly affect the software development process. Many of these factors are difficult to predict or control in advance, yet they can have a decisive impact on a project’s outcome.
On our projects, we’ve faced several such risks that had a major influence on the outcome:
| Risk | Consequences |
| Shifts in business priorities and market conditions | Resource conflicts, extended timelines, reduced team motivation, lower product quality, and increased tension between stakeholders |
| Mid-project budget reductions | Compromised product quality, contractual challenges with vendors, and weakened stakeholder confidence |
| Introduction of an additional vendor | Duplicated efforts, contractual disagreements, wasted time, and budget inefficiencies |
| Mergers and acquisitions | Extended timelines, revised requirements, added pressure on teams, uncertainty in delivery, and communication challenges |
As mentioned earlier, most of these risks can’t be fully predicted or controlled. Any of them may lead to a project being paused or canceled. But consistent communication between stakeholders and the development team, realistic planning, and a flexible project management approach can help mitigate the impact of project disruptions.
When we worked on Lilypad, a location-based chat app, we had to address reassessed goals driven by market assumptions, which led to multiple changes in feature scope and functional requirements.
To reduce disruption, we applied a flexible project management approach:
Requirements were treated as adjustable rather than fixed, allowing the team to respond quickly without compromising delivery quality.
As a result, the client successfully launched the product. Over 1,300 users downloaded the app within the first few months.
Technical risks are challenges that can arise during development due to technical factors. In this group, we highlight risks related to technical aspects, third-party integrations, UI/UX design, and security.

In our experience, most critical technical risks arise from architecture, the tech stack, and technical decisions. If you overlook these areas early, the cost of fixing mistakes grows quickly.
We most often see the following technical and architectural risks:
| Risk | Consequences |
| Architecture misalignment with business and technical requirements | Performance issues, scaling limitations, increased maintenance effort, and higher long-term costs |
| Technology stack misalignment | Slower development, hiring challenges, reduced performance, and expensive long-term support |
| Outdated or unsupported technologies | Security vulnerabilities, compatibility issues, limited upgrade paths, and growing technical debt |
| Inexperienced development teams | Fragile implementations, logical errors, architectural shortcuts, and costly rework over time |
In most cases, responsibility for architectural and technology decisions sits with a technical leader on your side. This can be a CTO, a senior developer, or a product owner with a strong technical background. Their role is to ensure that architecture and technologies align with your product vision, business goals, and growth plans.
At Clockwise, we reduce technical risks by reviewing and shaping the app’s architecture, validating the technology stack, and identifying weaknesses before they become costly problems. Depending on the project’s needs, our clients receive input from experienced backend and frontend engineers, architects, QA specialists, and product experts who regularly build similar systems.
We have built and launched products with 100+ third-party integrations, including payment systems, analytics platforms, social networks, marketing tools, and other external services.
Here are the most common integration risks we have faced:
| Risk | Consequences |
| Outdated or inconsistent documentation | Slower development, misunderstandings during implementation, and unexpected rework |
| Security risks when integrating external services | Increased exposure of sensitive information, compliance concerns, and potential vulnerabilities |
| Impact on application performance | Added latency, service outages, degraded user experience, and reduced reliability |
Each third-party integration presents its own technical and product challenges. We never assume that an API will work exactly as described or cover all real use cases.
Our team starts by reviewing documentation with a critical eye and validating key scenarios before full development begins. When needed, we communicate directly with third-party support teams to clarify limitations and edge cases. Most importantly, we test integration ideas early during discovery.
Such an approach will help keep development predictable.
A social media marketing agency owner came to us because their team relied on several disconnected tools with limited functionality. Switching between platforms slowed their daily work and complicated internal processes. They wanted a single, custom software solution to bring everything together.
To solve this problem, we built a unified platform with integrations for Instagram, Facebook, Twitter, and LinkedIn. The marketing team could schedule and publish posts from a single interface, design visuals using built-in Canva support, and manage content approvals without leaving the system.
We reduced integration risks early by researching each social media API during the discovery phase. Our team analyzed documentation for specific scenarios that the product needed to support. After that, we built several small proof-of-concept integrations to validate them.
These early checks confirmed feasibility and helped us choose the right technical approach. As a result, we met tight deadlines, delivered an MVP quickly, and avoided extra time spent on fixing integration issues later.

For each of the 200+ software projects in our portfolio, we had to build a reliable security system.
Here are the risks we run into most often in our projects:
| Risk | Consequences |
| Reduced testing coverage | Weak authentication and access control, unstable security posture, production incidents, emergency fixes, and loss of user trust |
| Unclear project vision for security and access | Incorrect permission models, inconsistent security rules across features, misaligned threat coverage, and expensive late-stage rework |
| Weak access control and permission design | Excessive user access, larger impact from compromised accounts, difficulty detecting misuse, permission sprawl, and higher risk of data leaks |
| Third-party integrations introduce hidden vulnerabilities | Inherited security flaws, data exposure, operational disruption, and potential compliance failures |
While developing highly secure software is complex and costly, there are three basic security goals that must be met. These are
Together, they are known as the CIA triad.
We begin security actions at the pre-requirements stage of the software development lifecycle (SDLC) to establish a foundation for all subsequent activities, from requirements gathering through testing and maintenance.
We also treat security as a quality attribute. That means we define acceptance criteria and keep checks running throughout development.
Continuous monitoring and evaluation help us catch issues sooner, respond faster, and release a safer product.
On our projects, we often manage security constraints that require balancing strength and cost. When we worked with BackupLABS, a platform that enables users to back up data from services such as GitHub, GitLab, and Trello, we had to research reliable, cost-effective methods to protect sensitive data.
Because the platform centers on user data, we focused on encryption from the start. We implemented end-to-end encryption using the AWS S3 Encryption Client and leveraged AWS KMS to encrypt keys across services. All encrypted client data is stored on Amazon servers, so even the development team doesn’t have access to it.
Some projects require even more attention at the planning stage. During the discovery phase for a cost estimation platform, we engaged a security consultant because the client prioritized security. We delivered clear, proven recommendations to reduce the chance of leaks and breaches. We used OWASP guidance and CIS Benchmarks to shape requirements and controls, and to keep the security plan practical and testable.

As we deliver projects with a 90–95% bug-fix rate, we understand the importance of QA and the risks it entails. When teams underestimate QA, issues rarely stay small. They compound, slow you down, and affect your product’s credibility.
Below are the most common risks we see when QA receives insufficient attention.
| Risk | Consequences |
| Defects reaching production | Broken user flows, crashes, incorrect results, support overload, emergency fixes, lost user trust, and significantly higher post-release fix costs |
| Rework consuming development time | Slower delivery, unreliable planning, and progress that depends on when hidden problems surface |
| Unclear product stability | Stressful releases, fear of change, delayed updates, and reduced ability to iterate and compete |
| Inconsistent user experience | Functionality that works for some users but fails for others, brand damage, and increased churn |
| Higher long-term costs | Urgent fixes, extended support effort, partial rewrites, and total costs that exceed early investment in structured testing |
Building the software testing process the right way helps you avoid the risks linked to poor product performance. From our experience, the most effective approach is to integrate testing practices into every stage of development.
When QA starts alongside development, you identify issues as soon as they appear:
This approach consistently improves quality and keeps timelines predictable across projects we deliver. You shouldn’t treat testing as a separate, pre-launch phase. It should be integrated into the development routine.
During the development process, we see a lot of risks associated with UI/UX design elaboration:
| Risk | Consequences |
| Misaligned user needs | Low user satisfaction, weak adoption, and designs that miss real user problems |
| Skipping early design stages | Misalignment between stakeholders, designers, and developers leads to costly and time-consuming rework |
| UI libraries that stop fitting | Mid-process replacement or heavy customization, wasted effort, and delivery delays |
| Underestimated custom elements | Slipped timelines, increased implementation effort, and planning inaccuracies |
| Overloaded visual designs | Slower load times, degraded performance, user frustration, and higher drop-off rates |
| UI over UX focus | Interfaces that look polished but feel difficult to use, reduced usability, and lower engagement |
| Missing screen states | Frontend teams forced to invent states, redesign cycles, and additional re-coding |
| Weak designer-developer communication | Rework, misinterpretation of designs, and missed delivery deadlines |
From our experience, most UI/UX design risks become manageable when you address them during the discovery phase. This is where we help you think ahead and set clear boundaries before design work accelerates.
At this stage, we:
Plan for change. We design with future updates in mind so the interface can evolve without forcing redesigns.
Account for complex design. We identify components that may require extra effort and reflect this in scope, timelines, and estimates.
Avoid performance-heavy visuals. We choose design solutions that look clean and work fast, without overloading the interface.
Turn research into clear requirements. We research design options, validate assumptions, and document decisions in a structured set of requirements that is understandable to everyone.
In our projects, we always recommend keeping the initial design simple. We see the best results when design evolves together with functionality, not ahead of it. This approach helps you allocate resources wisely.
Over the years, we’ve refined a set of design practices that help us deliver predictable results, avoid rework, and keep design aligned with both user needs and technical realities:
We reviewed 2 major risk categories and explained how we handle them based on our hands-on experience. We now explain how we conduct risk management in software engineering across the full range of risks across our projects.
We document risks in a risk register. In simple terms, the risk register is a table that lists risks, including their names, status, probability, mitigation plans, and other key attributes. It helps identify potential risks early, plan to avoid them, and reduce their impact if they occur. The project manager owns the risk register and creates it during the discovery phase.
Here is what a typical risk register looks like in our projects:
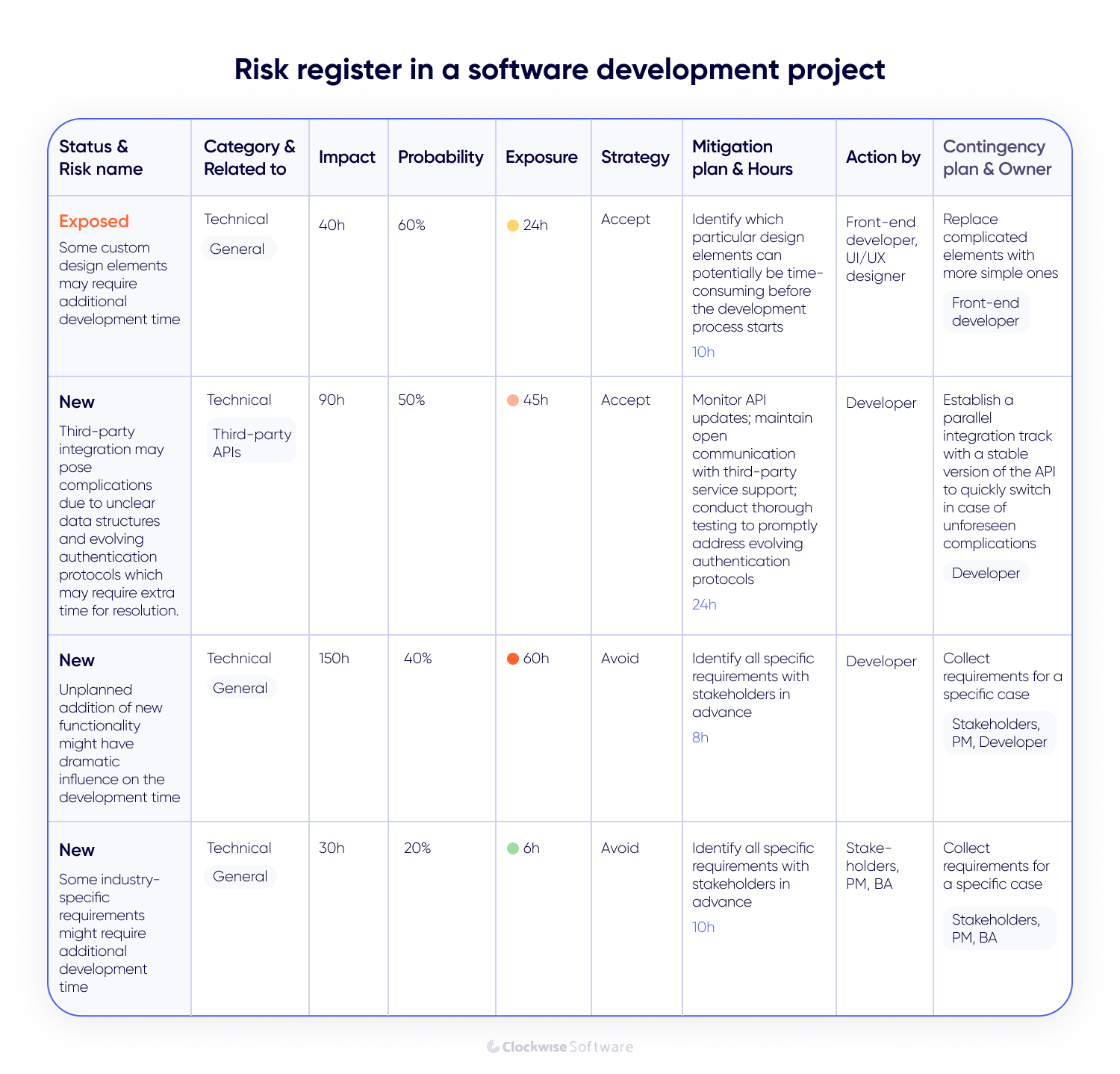
At Clockwise, we manage risks through the following steps.
Planning risk management. We align with stakeholders and team members on the risk management process and schedule related activities. The risk management plan defines risk sources and categories, impact and probability metrics, and the overall mitigation approach.
Identifying and categorizing risks. This step focuses on identifying risks that may affect project delivery and recording them in the risk register. We typically uncover risks through stakeholder discussions, collaboration with the development team, brainstorming sessions, analysis of historical data, SWOT analysis, risk checklists, and similar methods.
Analyzing risks. Next, we assess and prioritize the identified risks. We assign a numerical value to each risk to reflect its severity. Quantitative risk analysis includes the following elements:
Impact (h). The potential severity of the risk is measured in hours of possible loss or rework.
Probability (%). The likelihood that the risk will occur, expressed as a percentage.
Exposure (h). The expected loss resulting from the risk is calculated using the formula below.
Exposure (h) = Impact (h) x Probability (%)
Mitigation (h). The estimated number of hours required to reduce or control the risk.
Risk assessment combines vulnerability analysis with an evaluation of potential impact to determine the overall risk level.
Planning risk response. We define actions needed to reduce or manage negative effects on the project. Here are the common strategies we choose from:
Elimination. We use this option when we can eliminate the risk quickly without additional resources.
Transfer. We used this approach to meet a client’s requirement for stronger protection against hacking.
Mitigation. When elimination is not feasible, we develop a mitigation plan to limit the impact.
Acceptance. Acknowledge the risk and prepare to handle its consequences. We use this strategy when mitigation would require disproportionate time or resources.
We apply mitigation to most risks. In some cases, a single risk may require a combination of strategies.
After selecting a strategy, we create a detailed implementation plan with defined tasks, owners, timelines, budget considerations, and supporting details.
With this guide on risk management in software development, you are already better prepared than many teams that address risks only after problems appear. This puts you in a strong position to protect your project and make more confident decisions throughout development:
We manage software development risks every day. Our team works with well-established processes and is ready to take ownership of your project. We will help you identify, reduce, and manage potential risks in a structured and transparent way to ensure stable delivery and alignment with business goals.
