- There are different risk categorizations, but technical and organizational risks are the most common categories in the IT field. Technical risks refer to technical processes, third-party integrations, design elaboration, and security, while organizational risks are connected with software development requirements, constraints, dependence on external teams, and stakeholder management.
- Risks, as well as the risk management process, are an inevitable part of any software development project, independent of the project’s size or complexity and the team’s level of expertise.
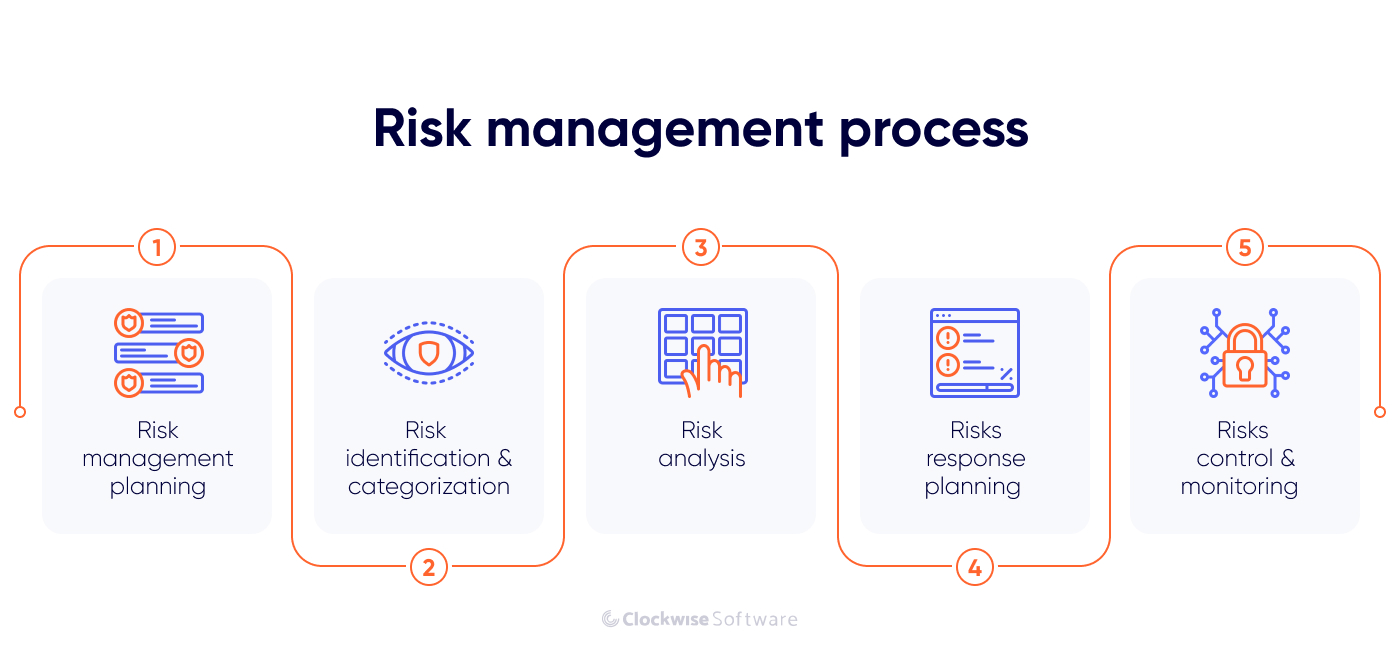
- Software development risk management in software development is a five-step process: planning, risk identification and categorization, risk analysis, risk response planning, and risk monitoring and control.
- You can’t identify all risks during the discovery phase; that’s why risk management is an integral part of the software development lifecycle.
The biggest risk is not taking any risk... In a world that’s changing really quickly, the only strategy that is guaranteed to fail is not taking risks.
In the early days of Facebook, Zuckerberg and his team faced risks at every turn, from addressing privacy concerns to scaling infrastructure to accommodate millions of users. Yet, they kept adapting and learning from their mistakes. This willingness to embrace risks transformed Facebook into the digital giant we know today and changed the way people communicate online forever.
Risks are an integral part of any custom software development project: it doesn’t matter if you are the world’s social media leader or a startup owner. However, any risk that isn’t identified and managed may turn into an issue. That’s why it’s important to develop a consistent approach to risk assessment for software development and mitigation for each project.
In this article, we explore the main software development risks and how they are classified and managed. We also share our own risk management experience that we have gained working on 190+ projects over the course of 9+ years.
Identifying and mitigating software development risks
Before we proceed to exploring software development risks, we need to define what a risk actually is.
The Project Management Body of Knowledge (PMBOK) describes a risk as:
An uncertain event or condition, that, if it occurs, has a positive or negative effect on a project’s objective.
In software development, anything that poses a threat to the project’s schedule or cost, or to the quality of the product, can be considered a risk.
PMBOK outlines the following software development risk categories: technical, external, organizational, and project management. There are also more detailed risk categories that may include legal, environmental, and other groups of risks. Risk categorization depends on the project specifics and industry. In the IT field, the most common risk groups are technical and organizational — these are the risks that we most often encounter on our projects.
The negative effect may or may not happen. But our goal is to foresee as many risks as possible, categorize them, and decide on a risk management strategy. This is exactly what we will explain in this article. You’ll get acquainted with the most common categories of risks in software development, how they can be eliminated, and how you can manage risks on your project.
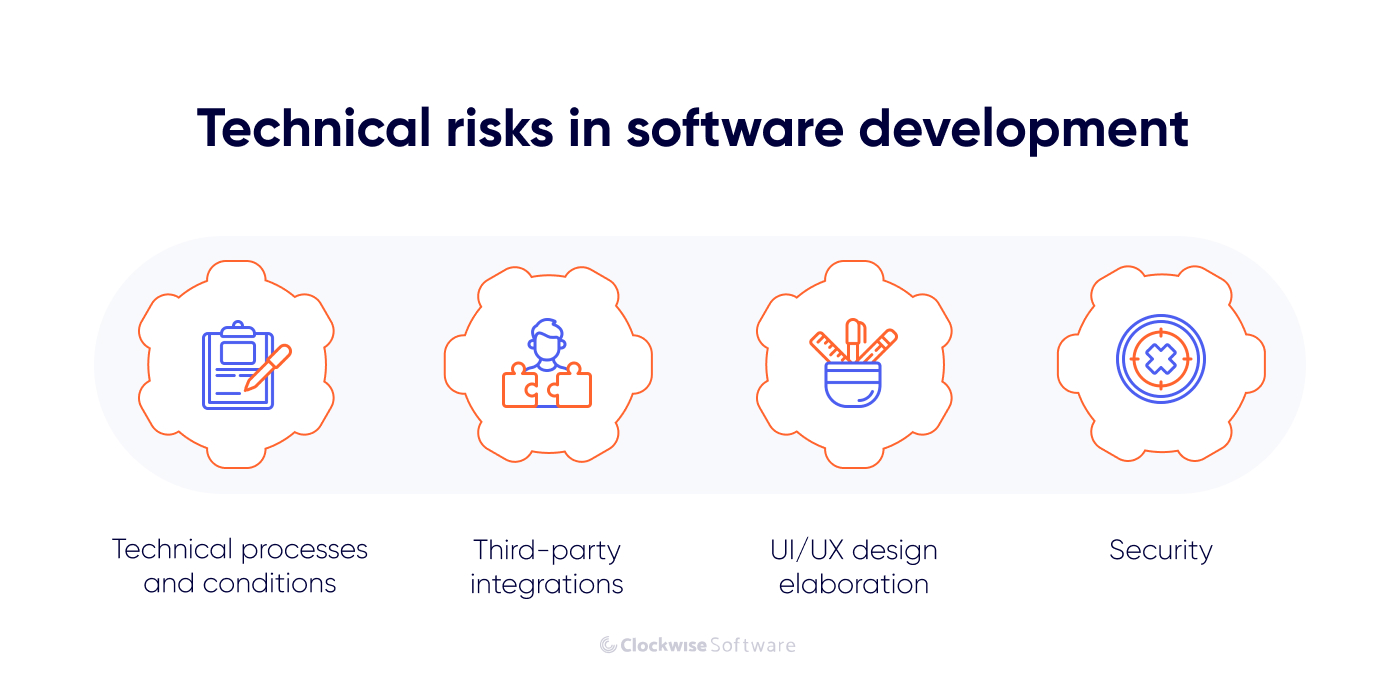
Technical risks to consider
Technical risks refer to challenges that can arise during the development process due to technical factors. In this group, we highlight risks associated with technical processes and conditions, third-party integrations, UI/UX design elaboration, and security. They all require your attention, so let’s take a closer look at each.
-
Technical process and condition risks
In software development projects, the most essential considerations are related to technologies and organization of the development process. We can highlight the following risks associated with technical processes and conditions:
- A development methodology that isn’t aligned with the project’s goals and complexity can impact the project’s success, budget, timeline, and overall quality.
- A poorly chosen technology stack can lead to issues with product performance and maintenance challenges.
- Use of outdated or unsupported tools and technologies can lead to compatibility issues and security vulnerabilities.
- Lack of testing, inadequate testing methods, or insufficient testing may lead to undiscovered bugs and software performance issues, resulting in poor quality of the final product.
- An architectural design that isn’t aligned with the app’s technical and business requirements may cause performance issues and difficulties in scaling and maintaining the software product.
- Software made without scalability in mind often poses significant difficulties in dealing with increased loads and user demands, resulting in performance degradation and frequent system crashes.
- Hiring inexperienced software developers may compromise code quality, leading to numerous logical errors that require a significant amount of unplanned work to fix.
Managing these risks requires deep, project-specific expertise.
Solution: The majority of risks associated with technical processes and conditions should be managed by the technical leader within your team. This can be a senior developer, a product manager with a technical background, or the CTO. However, in some cases, your software development team may lack the necessary expertise, making it challenging to deal with these types of risks.
The optimal way out of this situation is software development consulting to get professional advice from a team of experts that are regularly involved in the development process. Depending on your situation, you may benefit from industry-specific insights from a team consisting of a project manager, UI/UX designer, business analyst (BA), backend and frontend developers, and QA engineers. You can take advantage of software development consulting to reduce technical process-related risks associated with your choice of technology stack, architectural design, and so on.
Building the software testing process the right way may help you to avoid risks associated with poor product performance. From our experience, we can say that integrating the software testing lifecycle (STLC) into the software development lifecycle (SDLC) helps ensure the high quality of the final product and identify issues and errors as soon as they arise. Read our STLC guide if you want to find out more about the topic.
-
Third-party integration risks
Nowadays, third-party integrations can be seen in the vast majority of products that we use for our work and in our daily lives. Can you remember the last time you had to register in an application from scratch without the ability to sign up from your Facebook or Google account? As a rule, third-party account sign-up/sign-in is the simplest integration included in an application.
When building such services as customer relationship management platforms, marketing automation platforms, or email marketing services, you will likely need integrations with social media platforms, analytics tools, lead generation tools, and others. This greatly simplifies the work and allows you to avoid duplicating information. So, it’s safe to say that modern software development projects can’t do without integrations.
However, there are a lot of nuances and pitfalls associated with integration of third-party services.
- Outdated, inconsistent documentation (such as instructions, guides, and other information given by third-party service providers to guide developers in integrating their services) can lead to integration challenges and require additional development time.
- Integration of third-party services entails security risks, since it implies sharing sensitive data with external providers.
- Integrating a third-party service can affect the application’s overall performance, as you can’t control the functionality of the service you want to integrate. For example, integrating a third-party payment service may introduce latency issues due to the service’s response time.
Solution: Each third-party integration is specific and typically requires a narrow approach to addressing integration risks. In some cases, you may need to contact the support team of the service you want to integrate in order to manage issues associated with incorrect functionality.
In our experience, we have had numerous projects that required integrations with other services. We illustrate the integration process in our Attention Experts case study. The owner of a social media marketing agency came to us with a problem: the Attention Experts marketing team used software with limited functionality and had to switch between a number of SaaS tools to manage their workflow, which hindered their internal processes. So, they decided to create an all-in-one custom social media marketing tool to optimize their everyday marketing tasks.
To meet this request, we created a tool that included integrations with Instagram, Facebook, Twitter, and LinkedIn. Thanks to this, SMM specialists were able to effortlessly schedule and publish posts on these social media platforms using an internal editor, work with Canva visuals inside the platform, and streamline content approval.
By performing preliminary research of APIs during the discovery phase, we reduced most risks associated with integrations. We investigated capabilities of third-party social media platforms by thoroughly researching API documentation for specific cases we needed to cover. After that, we implemented several simple Proofs of Concept (PoCs) — demonstrations aimed at validating an idea and deciding on the best way to bring it to life.
These PoCs allowed us to ensure that we could use integrations provided by these social media platforms.
Thanks to that, our team succeeded in meeting tight deadlines (our client wanted to get the platform MVP as soon as possible) and didn’t have to dedicate additional time for risk management.
-
UI/UX design elaboration risks
Elaborating a UI/UX design means creating the interface through which users will interact with your app. The UI/UX design also determines how easily users can accomplish their goals using your application.
In our projects, we have faced the following risks associated with UI/UX design elaboration:
- Failing to understand and address the actual needs and expectations of your target audience can lead to a design solution that doesn’t resonate with users, resulting in poor user satisfaction and adoption.
- Skipping the moodboard and wireframing/prototyping stages may lead to misunderstandings between stakeholders and the development team, which can entail costly and time-consuming design rework.
- Selected UI libraries/templates may no longer be applicable when the design changes.
- Some custom frontend elements may require additional development time.
- Intensive designs can slow down the application, leading to a poor user experience and potentially high bounce rates.
- Focusing on the user interface without paying enough attention to the user experience may result in an application that isn’t user-friendly.
- Not elaborating different screen conditions (normal, active, error, hover, etc.) during the design process means that frontend developers have to create them on their own. This may require additional time for re-design and re-coding.
- Poor communication between UI/UX designers and frontend developers may lead to rework and missed deadlines.
Solution: You can foresee and mitigate most risks associated with UI/UX design elaboration during the discovery phase. At this stage, you can:
- plan how to make your design future-proof
- take into account all design elements that may require additional time
- consider how to avoid intensive design elements that will slow down the application
- research the best design solution and turn the results of this research into solid requirements outlined in a software requirements specification (SRS)
Based on the requirements, a UI/UX designer should create a wireframe that demonstrates the product’s key design elements. This wireframe should serve as a preview of how the final product will look, allowing stakeholders to approve the concept before it turns into a realistic interactive prototype. Design elaboration as an iterative process allows you to make sure that the product’s interface looks as expected.
At Clockwise Software, we always emphasize design simplicity for the MVP. A product’s design should evolve along with updates to product functionality, not vice versa. This contributes to smart resource allocation and allows our clients to make sure that the design is in line with their expectations.
In our experience, we have seen a lot of situations that emphasize the importance of a minimalist design for the MVP. For example, on one of our projects, the client wanted a catchy and attractive design for their application that would strongly distinguish the product from competitors. In order to fulfill the client’s requirements, our designers mixed different styles and dozens of shades to create a unique and unusual user interface. However, it turned out that this design solution was too much for the MVP’s simple functionality, and the user experience suffered. As a result, we had to completely rework the ready-made design to make it more minimal and user-friendly. This required additional time and budget.
It’s also important to follow design trends to stay on par with competitors. To ensure that your app’s UI/UX design stays up to date, you need to consult with your designer and implement a thoughtful approach to design trends.
-
Security risks
Security is a major concern in software development. Users always expect software they use to protect their data. However, some product owners don’t pay enough attention to their product’s security, preferring to focus on monetization and functionality first.
There are a significant number of famous cases where improperly managed security risks led to terrible consequences. For example, the Equifax data breach.
Equifax is one of the three major credit reporting agencies in the United States that is responsible for collecting and maintaining financial data on millions of consumers. In September 2017, Equifax suffered a massive data breach that exposed the personal and financial information of approximately 143 million Americans. The breach included sensitive data such as names, Social Security numbers, addresses, and even credit card numbers.
There were several preconditions that led to the Equifax breach:
- Equifax confirmed that they failed to apply a security patch for a known vulnerability in the Apache Struts web application framework. Hackers detected this vulnerability and used it to gain access to Equifax systems.
- Equifax didn’t detect the breach for several weeks. Slow detection and response led to data leaks, leaving people unable to take immediate steps to protect their personal information.
- Reports revealed that Equifax used default usernames and passwords for key systems, making it easier for attackers to gain access.
We can also highlight the following security risks from our practice:
- Tight deadlines may lead to a lack of testing, and, as a result, the creation of an unstable security system.
- An unclear project vision may lead to an inadequate understanding of how the product’s security system should operate.
Solution: While developing highly secure software is complex and costly, there are three basic security goals that need to be met one way or another. These are confidentiality, integrity, and availability. Together, they are known as the CIA triad.
Security actions should be taken at the pre-requirement stage of the software development lifecycle (SDLC) to establish the basis for all actions, from requirements gathering through testing and maintenance.
Since security is considered a quality attribute, it’s also necessary to conduct software quality management from the very beginning of project development.
Addressing, analyzing, and mitigating security risks brings a variety of advantages. Continuous monitoring and evaluation through software and web application scanning tools can lead to early detection of errors or problems, timely implementation of appropriate actions in response, and the launch of a secure software product. Otherwise, security risks may become more problematic in the future.
On our projects, we have had to manage a lot of challenges associated with security. For example, when working on BackupLABS, we had to conduct thorough research to find a reliable yet cost-effective way to provide superb security. BackupLABS is a platform that allows users to back up their data from a variety of services like GitHub, GitLab, and Trello.
Naturally, for such a data-focused service, we had to ensure reliable encryption. For this, we provided end-to-end encryption with the AWS S3 Encryption client and used AWS KMS to enable encryption of keys for different services. In this way, we mitigated the risk associated with possible personal data leaks, as no one can access the client’s encrypted data (even developers).
All encrypted client data is stored on Amazon servers, so even the development team doesn’t have access to it.
In some of our projects, the software security system has required even more attention. When carrying out a discovery phase for the owner of a cost estimation platform, we involved a security consultant. Since our client prioritized security as one the key tasks, we had to provide proven recommendations on how to eliminate data leaks and breaches. As a result, we leveraged OWASP and CIS benchmarks — industry-specific practices — to ensure high-level security.
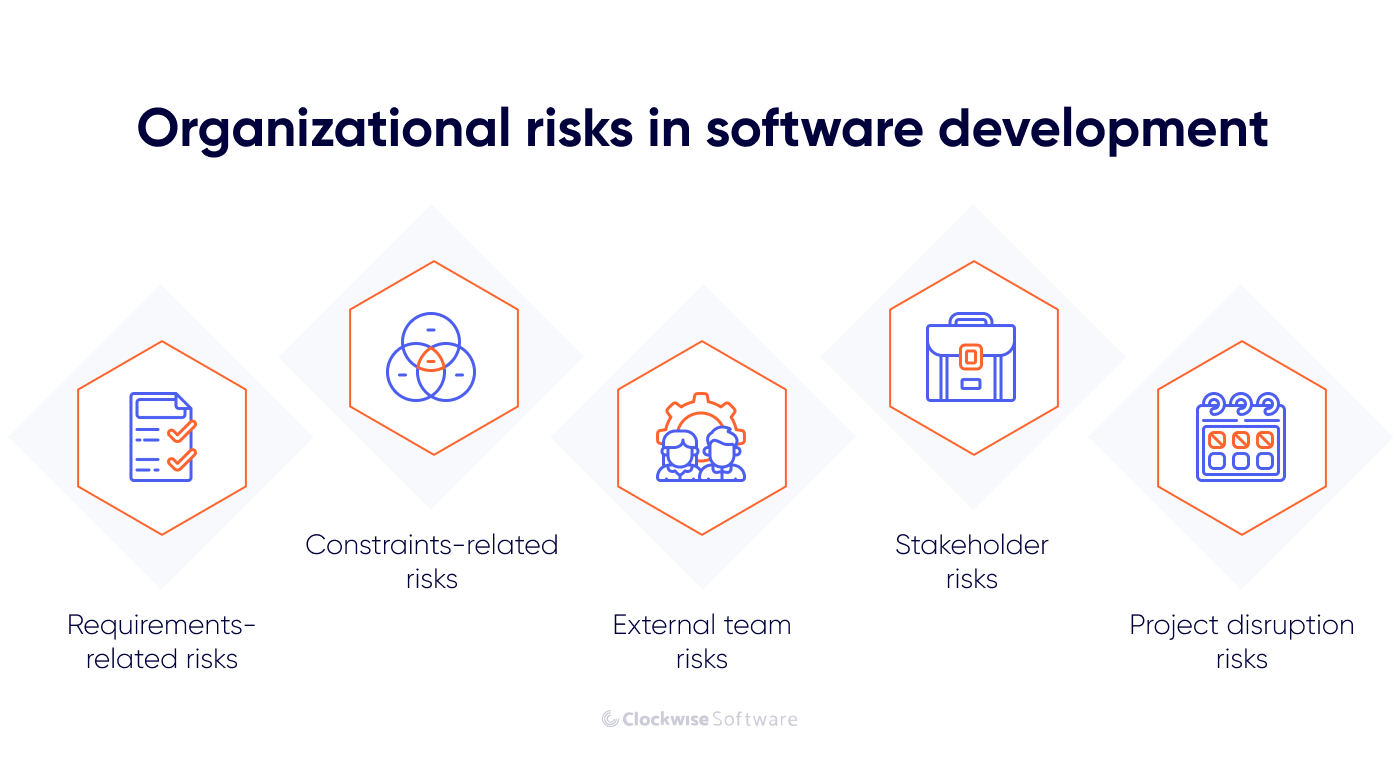
Organizational risks to pay attention to
Organizational risks refer to potential challenges that can affect a project’s success due to factors related to organization of the software development project. As we have worked on various projects with different teams and different collaboration models, we’ve often had to deal with the following risks.
-
Requirements-related risks
PMBOK defines requirements as quantified and documented needs, wants, and expectations of the sponsor, customer, and other stakeholders.
Requirements are a crucial part of any software development project and serve as a foundation for designing, developing, testing, and maintaining the software product.
According to the Pulse of the Profession study carried out by the Project Management Institute among 5402 companies, 35% of projects fail because of incorrect requirements collection. Thus, the importance of requirements can hardly be exaggerated.
ResearchGate discussed software development risks with designers, architects, and line managers of large software development organizations in four companies and highlighted seven risks associated with product requirements that align with our experience:
- When working on our projects, we have repeatedly encountered a client’s intention to add multiple requests in one requirement. Although we understand that this desire is driven by the intention to shorten the list of requirements and, consequently, reduce the development time and cost, our experience shows that clarity and prioritization are more likely to achieve these purposes.
- Inappropriate representation makes requirements difficult to understand. This includes requirements that contain pseudo-code, references to other documents, and other uncertainties.
- A requirement that is closely related to other requirements is susceptible to external influences or changes.
- Notes and assumptions in requirements may result in developing the wrong functionality.
- Unfeasible, unclear, or untestable requirements are hard to understand and implement.
- Poor adaptation to evolving requirements can cause delays and conflicting priorities.
- Deviation from the initial product vision in late stages of product development can impact on-time delivery and disrupt sprint planning and execution.
ResearchGate highlighted these risks as a result of a large study, and we at Clockwise Software have encountered all of them in our work. We can confidently state that unclear, inappropriately represented requirements often lead to misunderstandings within a team and result in a final product that doesn’t meet expectations. This entails thousands of dollars in rework, delays, and lost resources.
Solution: On our projects, we have faced all of the risks described above. In order to deal with them, we lay down requirements in the form of a software requirements specification (SRS) — a comprehensive and structured description of the requirements for a software product to be developed. An SRS allows us to get the most out of the requirements, making them clear, unambiguous, comprehensive, traceable, and properly presented. The SRS is a tool for communicating between stakeholders and development team members and acts as a structured framework for managing changes or updates to requirements.
At Clockwise Software, we establish an SRS during the project discovery phase — the pre-development stage of software creation focused on investigating, planning, and collecting all necessary documentation. The discovery phase encompasses collecting requirements, establishing the application’s structure, and compiling and approving requirements. This way, we can make sure that an SRS is made in accordance with the project’s business needs, has a clear and understandable structure, and provides an accurate and detailed description of each goal that needs to be met before development is finished and the final product sees the world.
Our article on how to lay down an SRS document will reveal this process in more detail.
To ensure effective requirements management, we also use tracking tools like Jira and Trello that help organize requirements in an agile manner. They allow our team to break down an SRS into smaller, more manageable tasks that can be prioritized, assigned, and tracked throughout the product development lifecycle. Such tools also foster more transparent communication between team members and allow everyone to stay updated on the project’s progress.
-
Constraint-related risks
Anything that slows down the software development process or interferes with achieving its goal may be considered a constraint. According to the triple constraint theory, there are three interdependent constraints influencing a product’s quality: scope, cost, and time. Changes to any of these constraints will invariably impact the others. Let’s take a closer look at each constraint:
Scope
Defining the scope of a software project is one of the most difficult tasks that needs to be done prior to the start of the development process.
As our experience shows, most proactive product owners have a broad idea of how their product should look. As a rule, they see their project in all its glory with a large set of features. However, most world-famous products began their journey as a minimum viable product (MVP): Spotify, Uber, X (formerly Twitter), and others. Therefore, we coach our clients in taking an iterative approach to creating the product of their dreams. We prioritize features, create a scope of work, and do the same for each subsequent product version. Still, there are a lot of factors that increase the risk of defining a non-realistic scope. The most widespread are as follows:
- Unplanned scope variations (like the addition of features that weren’t approved during the planning stage) may require additional development time and resources.
- Lack of agility makes it difficult to handle changes in the scope.
- Improper feature prioritization can lead to missed market opportunities.
Scope risk may lead to time and cost overruns, which may also result in a delayed product launch.
Time
The time constraint refers to the amount of time available to complete the project’s scope. It represents the deadline by which the project’s objectives and deliverables need to be achieved. Typically, the timeframe for project completion is calculated during the discovery stage and depends on the scope, but the risks of exceeding this estimate remain. In our experience, we’ve faced these risks associated with time constraints:
- In difficult projects, managing potential challenges is hard. That is why such projects are more likely to encounter delays.
- Miscommunication and misunderstandings within the team delay the project’s progress.
- Lack of resources or improper allocation of resources slows down project progress.
- Inaccurate planning and lack of consistency and accuracy in planning can lead to inadequate time estimates.
Time constraints, if not handled adequately, may result in missed deadlines.
Cost
Budget limitations for developing a new product or improving an existing one create cost constraints. Factors that may increase the risk of not finishing a project within the budget include:
- A poor budget allocation strategy, which may lead to cost overruns.
- Lack of attention to budget management from stakeholders, which may interfere with the creation of a cost-effective project development plan.
- Absence of project expense tracking throughout the software development lifecycle, which may lead to deviations.
- Lack of flexibility, which can make it difficult to adapt to changing circumstances and adjust the budget accordingly.
Cost constraints may necessitate increasing the budget to complete the project.
Solution: As our experience has shown, three constraints are always interconnected: limited time will result in a reduced scope, and a tight budget may extend the timeline. So, we have developed a strategy for balancing these constraints. For this, we define realistic project parameters, ensure a clear understanding of the scope among stakeholders, maintain a visible timeline, efficiently allocate resources, and continuously monitor progress while making necessary changes and adjustments. This dynamic approach allows for balanced decision-making and successful project outcomes.
-
Risks associated with external teams
In many cases, software development projects have to rely on external teams. There may be many reasons for that: the need for specialized expertise that is not available in-house (for example, in artificial intelligence or specific programming languages), the necessity to handle an increasing workload, the desire to optimize time and cost constraints, etc.
When involving external professionals in your product development, you may face risks such as:
- Poor involvement of external specialists in your project. This often happens when you hire freelance specialists whose work comes down to the mechanical execution of assigned tasks. Their lack of understanding of the product lifecycle and its goals may result in poor quality of the end product.
- Cooperation with unreliable agencies or companies without experience in your industry may lead to unsatisfactory outcomes and project delays.
- Sharing sensitive information with external workers poses a threat to data security and confidentiality.
It’s hard to control external teams that are not actually involved in your project and aren’t a part of your development team. The risk of not meeting project requirements and timeframes increases greatly when you have an unreliable partnership.
Solution: The most obvious way to eliminate this risk is to hire the necessary professionals in-house. This way, you have full control over your team and their workload.
However, in many cases, outsourcing development of the whole app or part of it is a wise decision. If you approach outsourcing correctly, you may not just avoid the aforementioned risks but also save time and money.
Delegating tasks to freelancers may seem tempting, as it is usually a cheap and simple option. However, there may be consequences. Although freelancers may be good specialists with a high level of motivation, their responsibility is questionable. Freelancers tend to work on several projects simultaneously and continuously look for new gigs, as this is the basic requirement of successful freelancing. This means that freelance developers are rarely dedicated to your task and may even switch to a different project in the middle of development.
Partnering with an outsourcing company is a far more reliable option, as outsourcing companies care about their reputation and long-term partnerships. When working with an outsourcing company, you get vetted developers with hard and soft skills that match your project requirements. Additionally, the outsourcing company creates conditions where workers can completely focus on projects, and a contract guarantees that you will receive the services you’ve ordered.
However, partnering with an outsourcing company still doesn’t guarantee your success. If you decide to delegate project development, you have to be very careful with selecting a contractor. Compare a few vendors, review their portfolios, and talk to representatives to make sure you can trust your application to a vendor. And never be lured by the lowest price, as it’s a red flag. We have described important steps in choosing the right app partners in a previous article. Check it out if you want to delegate development and focus on business-related tasks instead.
Software development outsourcing companies work on a contract basis, which reduces the risk of incorrect or untimely work. Such a contract typically outlines the rights, responsibilities, and obligations of both parties. If the software development company fails to comply with the terms of the contract, it will suffer from sanctions, which protects you from many risks related to external teams. Also, signing a non-disclosure agreement (NDA) is the most efficient way to protect your intellectual property and other sensitive information when working with third parties.
-
Risks associated with stakeholders
Stakeholders are people directly interested in the project’s positive outcome. When talking about software development, stakeholders may be people in your organization whose work will be influenced by introducing the new software. It’s a good idea to involve stakeholders in the development process, as their input helps you make better decisions to improve the software's effectiveness.
In software development, a product owner may represent all stakeholders, or stakeholders may be involved in the development process personally.
Stakeholders’ involvement in the project results in various project control risks:
- Insufficient involvement of the product owner/stakeholders in the development process leads to an inadequate understanding of project complexity and expected deliverables. Obviously, this leads to unrealistic expectations, rework, and delays.
- Lack of communication between the product owner/stakeholders and the development team can lead to misunderstandings, delays in decision-making, and, ultimately, failure to meet project objectives.
- Micromanagement — excessive control over the development process — is the reverse problem. It hinders the team’s ability to work effectively and make creative decisions, which in turn results in loss of motivation and poor productivity.
- Introducing new stakeholders in the middle of the development process also entails a lot of threats to the project’s success. Their lack of familiarity with the project’s history may lead to communication difficulties, as new stakeholders need to review the project’s scope and requirements, causing delays in decision-making.
- An unclear distribution of responsibilities among stakeholders sometimes lead to wrong decisions, which, again, increase the project’s timeline and budget.
Solution: A project manager doesn’t have the authority to make decisions that affect the fate of the product and project. They only communicate stakeholders’ decisions to the team, translate them into clear requirements, and manage their execution. Therefore, lack of established communication with stakeholders increases the risk of not getting the product you expect.
A RACI matrix helps manage stakeholders’ involvement in the development process, clarifying and communicating roles and responsibilities for tasks within the project. There are four key roles defined in the matrix:
- Responsible (R) — a person or group of people responsible for accomplishing the task
- Accountable (A) — a person or or group of people accountable for the task’s overall success
- Consulted (C) — an individual or group of people who consult, advise, or share their opinion or expertise for a certain task
- Informed (I) — a person or group of people who need to be informed about the task’s progress but aren’t directly involved in its accomplishment
Here is an illustration of how a typical RACI matrix can look in a software development project:
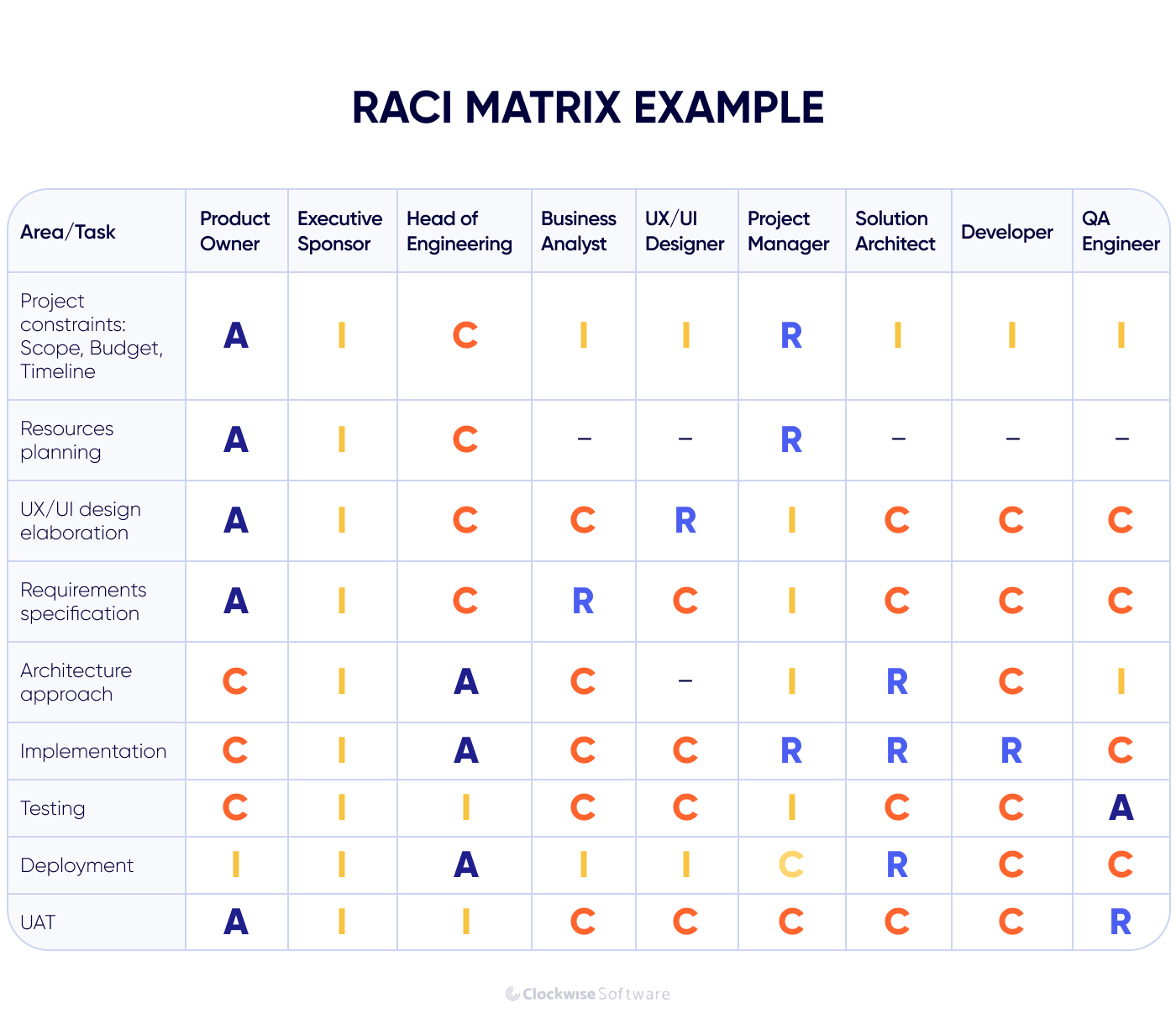
Each task the team starts working on should have defined roles. This way, you make clear who is responsible for certain decisions on the project and reduce the number of unauthorized changes and the amount of rework.
If you want to get precisely the product that meets your needs, you should involve stakeholders in project development from the beginning. It’s essential to set clear goals and establish and approve software requirements.
It is not necessary to conduct daily meetings with project managers and team members. However, regular meetings (weekly or biweekly) with the project manager or the whole development team will allow you to share the project’s vision and goals, check the project’s status, discuss task prioritization, etc.
-
Project disruption risks
There are a lot of factors that can cause global organizational shifts in the development process, and the majority of them can hardly be controlled or identified in advance.
On our projects, we’ve faced some risks that have had a major influence on the project’s fate:
- A dramatic shift in business priorities, market changes, and technological advancement can become a reason for project reprioritization. This may result in resource conflicts, have a significant negative impact on the project timeline, lower the team’s motivation, compromise product quality, and result in conflicts between stakeholders.
- Significant budget cuts in the middle of development require task reprioritization and resource reallocation. Naturally, this is detrimental to the quality and success of the end product, triggers contractual issues with the vendor, and undermines stakeholders’ confidence in the project’s success.
- Another vendor may be introduced into a running project due to an organization’s internal politics and personal preferences of key project stakeholders. This can be disadvantageous and problematic for both the company and the development team, as it leads to a waste of already invested money, time, and other resources as a result of conflicts and contract disagreements.
- When a company goes through a merger and acquisition process, this introduces a lot of complexities to the project, as it has a significant influence on strategic goals and often leads to changes in the ongoing development process. The acquiring company may revise contracts with existing vendors, reassess the budget, and introduce a lot of uncertainties to the development process. This leads to the inevitable extension of the project’s timeframes, puts additional pressure on the development team, requires revision of requirements, and leads to communication challenges.
Solution: As we’ve mentioned, most of these risks can’t be foreseen or controlled. But each may become a reason for the project to be frozen or even canceled.
We recommend reviewing a project’s concept, priorities, and business goals before starting software development. This won’t eliminate the possibility of any of these risks but can reduce their probability of occurrence.
Effective communication between the development team and stakeholders, careful planning, flexibility, and adaptability in the project management process can soften the consequences of project disruption.
How to manage risks
We have reviewed two large groups of risks and dozens of examples and have explained how we deal with them based on our own experience. In order to deal with all risks you may face during the software development process, you need a proper method of risk handling. In this section, we share how we manage risks in our projects.
Risk management is the process of identifying, addressing, and eliminating risks before they cause damage to the project. It is a continual process that spans the whole software development lifecycle.
Risks are outlined in the risk register — a dynamic document used for risk management. In simple words, the risk register is a table containing risks, each with a name, status, probability, mitigation plan, and other characteristics. It identifies software risks and plans to avoid them and minimize their effects if they occur. The project manager (PM) controls the risk register, which is laid down during the discovery phase.
Here is how a typical risk register looks in a software development project:
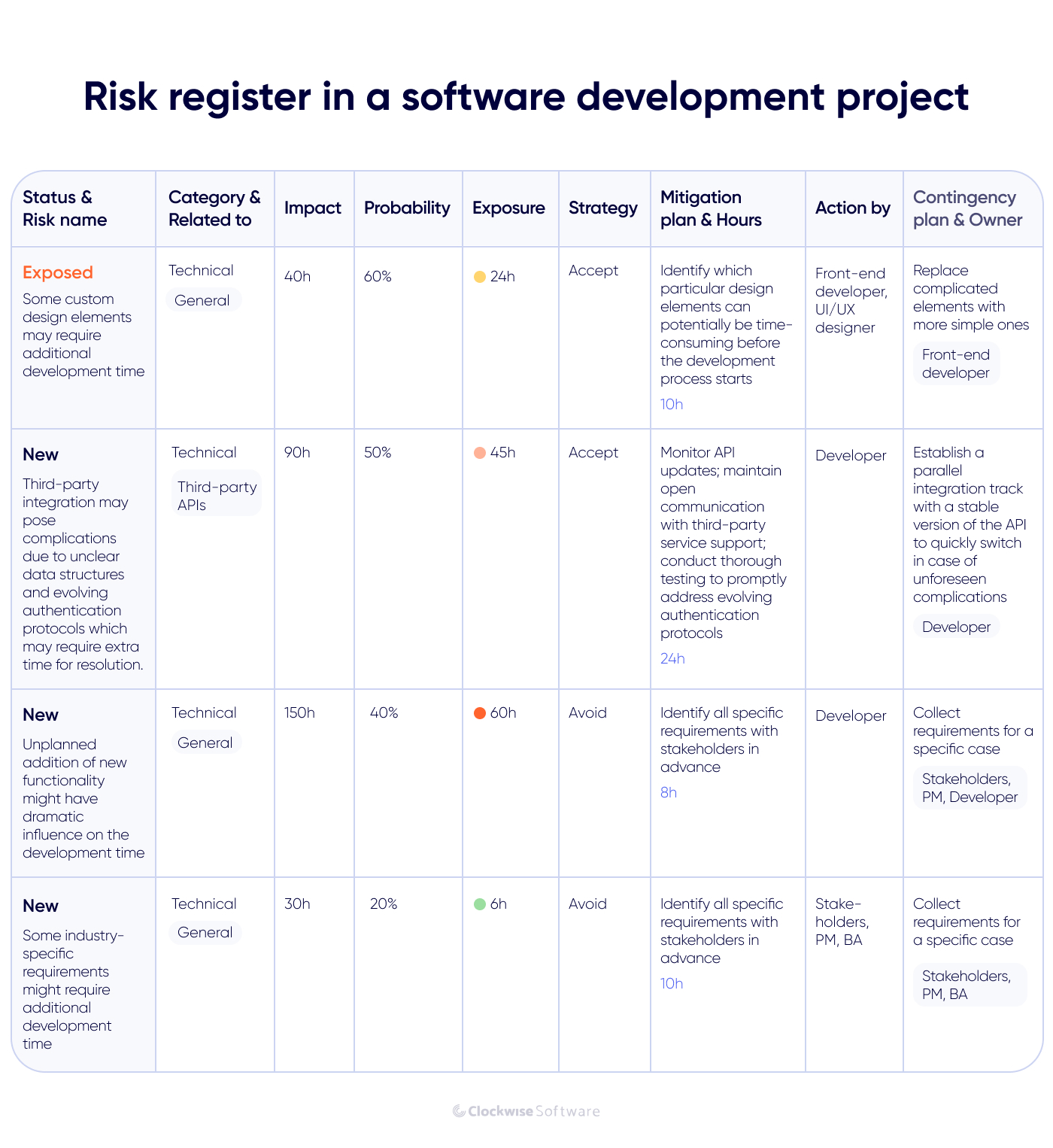
A proper approach to risk management is crucial, as it will define how effectively you can address risks that may affect your project. In our company, we conduct risk management the following way:
-
Plan risk management. At this stage, we plan all activities related to the risk management process: discuss the risk management process with stakeholders and team members, and schedule and organize risk management activities. A risk management plan includes definitions of risk sources and categories, risk metrics (impact and probability), and a software development risk mitigation plan.
-
Identify and categorize risks. This process refers to identifying risks that may affect project development and entering them into the risk register. Risks should be identified as early as possible. You can identify risks relevant for your project through communication between stakeholders and the development team, brainstorming sessions, historical data analysis, SWOT analysis, a risk checklist, and other methods.
Risk identification is one of the central subjects discussed during regular project status and reporting meetings, as it’s done throughout the SDLC.
-
Analyze risks. In this step, you need to assess and prioritize all risks identified during previous steps. This involves quantifying each risk’s severity on a numerical scale. Quantitative risk analysis involves assigning numerical values for the following:
-
Impact (h) — assesses the severity of the risk, (a measure of potential harm or loss that the risk can result in), quantified in terms of hours
-
Probability (%) — the probability of a risk’s occurrence, expressed as a percentage
-
Exposure (h) — the outcome of the impact and probability, quantifying the expected loss from the risk according to this formula:
Exposure (h) = Impact (h) x Probability (%)
-
Mitigation (h) — number of hours required to mitigate the risk
Software development risk assessment merges vulnerability analysis and threat impact evaluation to reach an overall conclusion of the risk level.
- Plan your risk response. Each risk needs to have a response plan — a set of actions that need to be taken to reduce threats that pose a negative impact on project development. This step can be divided into two parts: identifying a risk response strategy and creating a plan to implement it. There are several possible risk response strategies:
-
Elimination — Take a different approach to a task that eliminates the risk. We implement this approach when risks can be eliminated in a minimal amount of time without requiring additional resources.
-
Transfer — Delegate the risk to a third party. On one of our projects, we had to adhere to this strategy to satisfy our client’s desire to increase protection from hacking.
-
Mitigation — Develop a plan to mitigate the risk, reducing the likelihood of its occurrence. When a risk can’t be eliminated, we develop a risk mitigation plan to soften the consequences.
-
Acceptance — Allow the risk to remain and deal with potential consequences. If risk mitigation requires a significant amount of time and resources, we stick to this strategy.
The mitigation strategy is applied to the majority of risks. However, one risk may require several strategies.
Once a strategy has been selected, the next step is to develop a plan to implement it. This plan should include an outline of the required tasks, responsible individuals, timeline, financial support, and related details.
- Monitor and control risks. After risks have been identified and analyzed and the response plan has been generated, the next step is to monitor and control these risks. This involves assessing events that trigger the risks, activating response plans when necessary, and ensuring the ongoing effectiveness of response strategies. All these activities should be systematically monitored and reported through a risk management process.
In conclusion
Risk management should be a vital part of any software development project. Timely risk identification and analysis along with a carefully developed risk response strategy can minimize the negative impact of risks on the project’s outcome.
There are numerous approaches to categorizing risks in the IT field; however, there are two categories inherent to any software development project: technical risks that encompass everything related to technical processes, and organizational risks related to the development process.
A great deal of software development risks can be discovered at the earliest project stages. A proper approach to managing and identifying risks can prevent most risks from being realized. However, although risk management and mitigation start at the planning stage, they don’t end with it; that is why you should monitor current and upcoming risks right to the end of the SDLC. And the best way to do so is to create and manage a risk register.
Sources
- A guide to the project management body of knowledge (PMBOK guide) — A book that defines standard terminology and provides guidelines for project management.
- Security Risks in the Software Development Lifecycle, International Journal of Recent Technology and Engineering (IJRTE). The article presents a study of real-life practices employed in response to software security risks, reveals security risk management best practices, identifies pitfalls, and explores why these risks occur.
- Defining Technical Risks in Software Development, University of Gothenburg. This article defines technical risks in software development and summarizes software engineers’ views on technical risks based on three workshops with 15 engineers of four software development companies.
- Classification and analysis of risks in software engineering, Hooman Hoodat and Hassan Rashidi. This paper classifies risks in software development and explains software risk management concepts.
- Risk analysis and management, Lavanya, N., Malarvizhi, T. The article presents the structured risk management process followed at Nokia Siemens Networks.
- A practical risk management approach, Becker, Gregory M. The article explores risk identification and evaluation criteria and the risk management process.
- Risk factors in software development projects: a systematic literature review, Júlio Menezes Júnior, Cristine Gusmao, Hermano Moura. This paper identifies and maps risk factors in environments of software development projects based on 41 studies.



