AI solutions
What we do
Services
Experts in
How we work
When you build a product for your own personal or business needs, you plan, design, and develop functionality that simplifies routine processes and implement a well-thought-out software security approach to ensure none of your data is compromised.
When you build an app you will license to end users, the custom software development process is pretty much the same. Yet, you need to keep in mind the specifics of your audience to ensure the product’s usability and security. It won’t just be you and your team using the app: it will be non-technical users who get access to functionality and share their data. Thus, both the app’s functionality and users’ data should be well-protected.
When it comes to SaaS product development, software security is more significant than ever. When building a SaaS product, it should meet not only your needs but also the needs of all your customers. In turn, your SaaS customers may use your app to meet their end customers’ demands.
As your app scales, so do the security challenges: you have to protect a cloud-based product along with all the data you and your customers may collect, process, and store.
Instead of considering the security of a single product built for a single company, you now have to consider the security of multiple versions of your SaaS solution provided to multiple businesses and end users.
In this article, you’ll learn basic concepts and security methods, get acquainted with critical terminology, and find out how to put theory into practice to reach the highest level of SaaS app protection.
According to a Cloud Security Alliance survey conducted in 2022, 55% of SaaS executives admitted to facing SaaS security incidents — 12% more than in 2021.
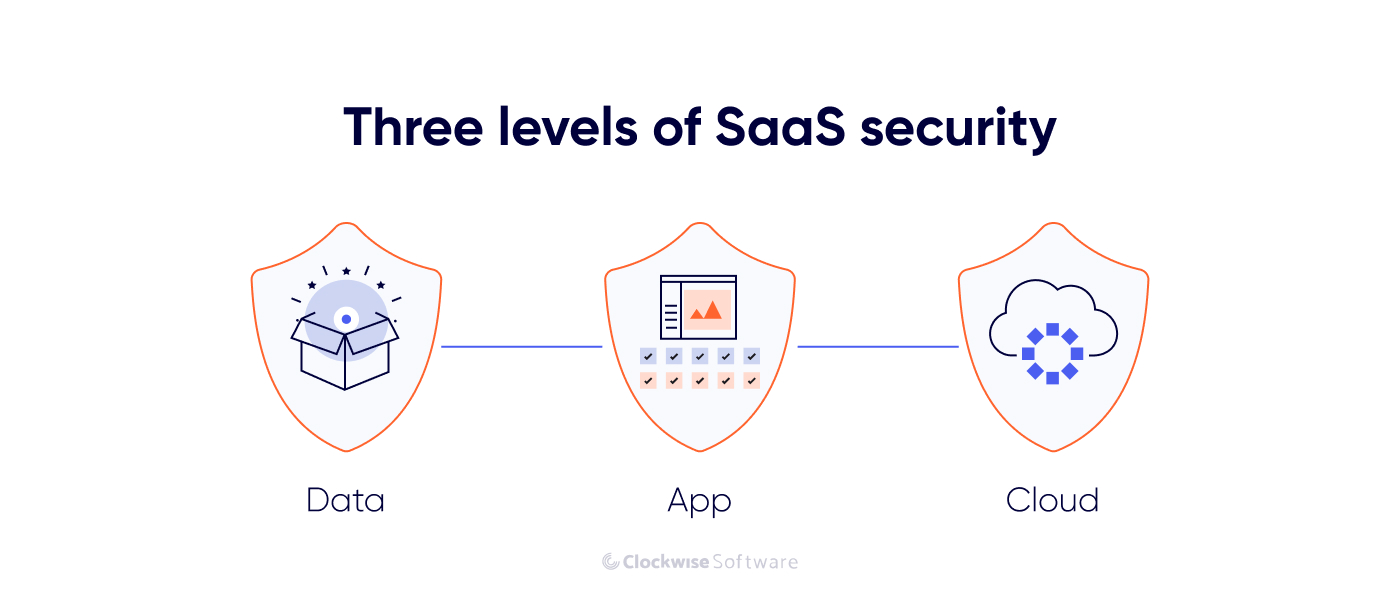
To avoid such incidents, you must ensure your security on three levels: data, app, and cloud. Let’s review how you can protect each level from threats.
Data is your customers’ most important asset, and it’s what SaaS users worry about the most.
In 2023, the global average cost of a data breach reached $4.45 million, a 15% increase over three years. Even though organizations worldwide are investing more in security than a couple of years ago, security breaches continue to bite companies’ reputations and budgets.
According to the SaaS model, your SaaS product development company collects, stores, and processes all customers’ data. Thus, you need to guarantee top-level security measures for all users.
We’d like to introduce the CIA triad to examine the concept of data security in more detail.
The CIA triad comprises three pillars of security: confidentiality, integrity, and availability. Let’s review all of them shortly.
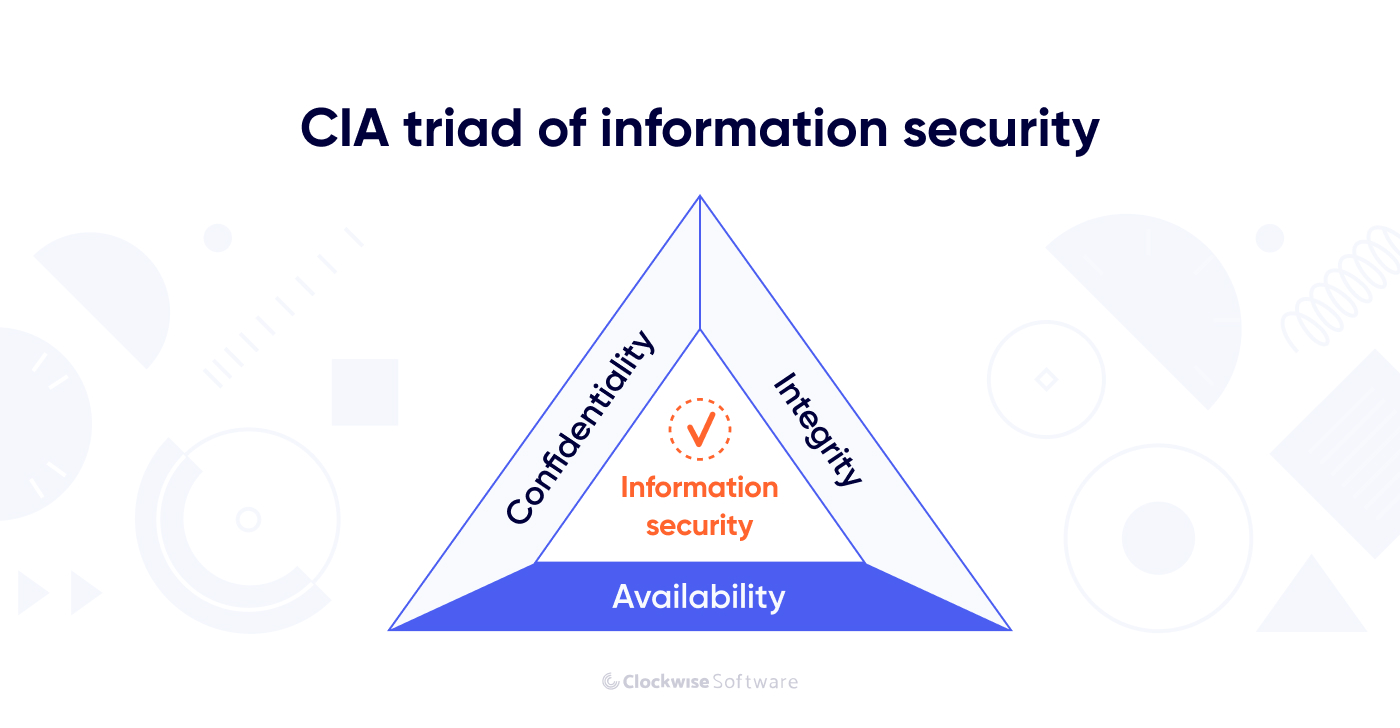
In most cases, to access your SaaS product’s functionality, users should be authorized in the software system. Individual users may need a login and password to access certain functionality. Corporate users can increase the security of their data through the setup of the software on their servers. Data accessibility depends completely on your app’s specifics, the functionality you provide, the data you collect, and the industry you operate in.
Preventing your system from unauthorized access is critical to keep the data confidential.
Data integrity is the accuracy, completeness, and quality of data as it’s maintained over time and across formats.
Data integrity is about ensuring that the information you collect and store is consistent and complete. This component of the CIA triad is essential for effective customer interaction, correct data analytics, and compliance with regulations like the GDPR.
Data availability ensures that data is provided to end users on demand. An app user should be able to access crucial data regardless of their current internet connection quality or the volume of data requested.
To secure the data your SaaS product collects, stores, and processes, you must adhere to confidentiality, integrity, and availability principles.
According to a Snow Software survey, the security of SaaS apps is the top priority of IT leaders in the US and the UK.
In most cases, SaaS products are distributed to users through an API (application programming interface). Imagine an API as a digital bridge connecting your SaaS product to your customer’s application. Just as bridges are vulnerable to floods and storms, APIs are vulnerable to a variety of security challenges.
Attackers may have an unlimited number of tools and methods available to attack your SaaS API, especially if it’s poorly coded.
You have to be ready to protect your application from unauthorized access and pay more attention to open-access scanning and access keys that users may use in public networks.
Typically, SaaS applications are stored in the cloud.
One of the specifics of cloud computing is that neither the SaaS provider nor the SaaS user has full control over stored data. Whether you choose AWS, Google Cloud, or another major cloud service provider, you won’t fully control all cybersecurity measures, as part of the responsibility for cybersecurity lies with the cloud services provider.
At the same time, you have to take into account challenges related to multi-tenancy — sharing certain components of a cloud environment between multiple users. Cloud misconfiguration, which may be caused by mistakes and poorly chosen settings during cloud set-up, is another common security concern.
Misconfiguration accounts for 21% of error-related data breaches.
Cloud hijacking occurs when an intruder gains access to a SaaS user’s credentials and may compromise the security of the whole product. Besides, a SaaS app may face injection attacks, insufficient cloud management, and many more issues.
DDoS attacks may take your servers down for hours, harming the data availability and integrity sides of the CIA triad, the SaaS user experience, and your company’s reputation.
A DDoS attack targets resources or services in an attempt to render them unavailable by flooding system resources with heavy amounts of unreal traffic.
DDoS attacks can affect all layers of a cloud system, including SaaS, IaaS, and PaaS, which brings us to the next level of potential security concerns: the cloud environment.
What can you do to protect your SaaS product? Let’s proceed with actionable plans to make your SaaS product secure, save your reputation, and provide your customers with top-level service.
Responsibility for SaaS product security may be shared between you, your SaaS users, and a cloud provider. While you as a SaaS provider take full responsibility for protecting your application and its infrastructure, SaaS users should be careful with their credentials and use caution when providing access to the product and sensitive data to third parties.
Now, let’s focus on your role in protecting your SaaS product.
As stated in the Project Management Body of Knowledge (PMBOK), it is much better to design security into software than to patch it in after the software is developed. Thus, you and your development team should prioritize software protection throughout the entire development process.
Your SaaS security journey starts with the project discovery phase. At this phase in the SDLC, your discovery team, headed by a business analyst, defines the product security policy.
The discovery team considers potential security threats and related risks and develops a mitigation plan.
A UI/UX designer now creates visual elements that align with defined security objectives. As the UI/UX designer creates the app interface for users with different levels of access, more security bottlenecks and concerns may arise.
Software development security includes two interconnected components:
Software engineers should implement the latest secure coding practices in the development process. Every component of the system should be built with security in mind under the guidance of an engineering leader, CTO, or software security expert.
Here are some common practices for coding secure software:
Software security testing pursues two key goals:
Continuous testing of your app’s security, along with frequent security training for your QA and QC department, may help you succeed at this stage of the SDLC.
There are multiple security testing methods your team may use:
Your SaaS solution will remain secure as long as long as you continue investing in its security. Engineering teams should follow security best practices not only during active development but also when deploying an app to the production environment, testing it with beta users, fixing bugs, maintaining it, and upgrading it.
Security should be your focus throughout the whole development process.
According to PMBOK, the SDL (secure development lifecycle) reduces software maintenance costs and increases software reliability.
If you have already started working on your SaaS app or plan to turn an existing application into a SaaS product, you can analyze your app’s security using app decomposition, threat modeling, threat prioritization, and third-party tool evaluation.
This method requires breaking down software into chunks to gain a deeper understanding of its architecture and possible attack surface.
Threat modeling is the way to identify potential dangers for your software system. This involves examining the overall application architecture, data flow, and potential vulnerabilities.
The next step is to prioritize threats based on their likelihood and severity.
If you use any APIs from third-party service providers in your product (such as AWS for cloud computing, Google Maps for geolocation functionality, Stripe for payments, or Twilio for chat functionality), you need to ensure their security.
In addition to those listed above, there are more security best practices you can implement in your SaaS product. Consult with a reliable technical leader or a dependable engineering team to discuss strategies that will help you protect your solution, reputation, and revenue.
In 2019, GPT-2 launched, the Cybertruck prototype was introduced, the IT industry was on the rise, and the COVID-19 pandemic was yet to begin. This was also the same year when Capital One, a financial company that had been operating for over 25 years in the US market, faced a $190 million security breach.
A hacker gained unauthorized access to the Capital One system and the personal information of more than 100 million US clients. The reason was a misconfiguration in a web app firewall. A tiny gap in application security affected millions of people.
But this isn’t even close to the biggest data breach on record. In 2021, more than 700 million LinkedIn user accounts were affected by a data breach. Meta (formerly Facebook) products have also suffered from security issues.
To help you do everything you can to ensure your and your users’ security, we’ve composed a list of best practices. Some of these may be obvious, but we believe it is important to mention them, as many companies still ignore them. Others may require significant changes to your company’s operations, including the app development process itself, but the security of your application and its users’ data is worth the effort.
Here, we describe processes and standards you should follow in your organization to minimize the risk of unauthorized access to your data. It is critical to start your security measures at this level:
Create a clear and comprehensive security policy outlining corporate and legal requirements, guidelines, procedures, and responsibilities for safeguarding your team, assets, data, and users.
Separate your corporate network from public networks to mitigate the risk of unauthorized access.
Use a unique domain name and enable domain name privacy protection to minimize chances of unauthorized access.
Data encryption allows you to encode text, audio, video, and other data so that it can’t be accessed, interpreted, or used by hackers. Use SSL to encrypt data exchanged between the server and the browser.
Implement encryption on corporate laptops and smartphones to protect sensitive data in case of device loss or theft.
Regularly assess and update the security measures of software tools used by your team to prevent data breaches.
Outdated operating systems on your corporate devices are prone to vulnerabilities. Keep operating systems across all devices and servers up to date to secure the data you store on them and exchange between them.
Require multiple forms of authentication to enhance account security. For example, you can require a password and a one-time code sent to an employee’s mobile device to enable access to an app environment.
Enforce the use of screen locks and password-protected screensavers to prevent unauthorized access to unattended devices.
Enforce the use of complex passwords that are difficult to guess and resistant to brute-force attacks.
Prohibit the sharing of user accounts and credentials to prevent unauthorized access and maintain individual accountability.
Set a regular reminder to back up data to ensure that data integrity and availability are maintained in the event of data loss or corruption.
Monitor and analyze system logs and audit trails to detect and investigate security incidents, anomalies, and suspicious activities.
Encourage responsible disclosure of security vulnerabilities by offering special programs to users or external researchers who identify and report bugs in your systems.
Create a detailed plan outlining steps to be taken in the event of a security incident, including incident detection, containment, eradication, and recovery.
This program may be of great value to new hires. Develop processes for securely provisioning and de-provisioning access to company resources to avoid potential risks.
The security measures described above should apply to every member of your organization and all vendors you work with, not just the development team. However, there are a few more measures that directly relate to the development process:
Be well-prepared for possible attacks, and make your team ready, too. Plan training sessions on how to respond to potential security threats.
As an example, consider Amazon’s cybersecurity awareness training.
Integrate the security considerations we described earlier into the software development lifecycle, from product discovery to deployment and beyond, to identify risks and respond appropriately.
Define coding standards and best practices that prioritize security, such as input validation, secure error handling, and secure data storage.
Evaluate candidates’ awareness of security principles and practices during the interview process to ensure a security-focused engineering team.
Bring aboard new team members with expertise in penetration testing to identify and address security vulnerabilities.
Conduct regular code reviews to detect security vulnerabilities and ensure compliance with security coding practices.
Continuously monitor and assess third-party dependencies for known vulnerabilities and risks to prevent supply chain attacks.
Use development tools designed for security, such as static code analysis tools and security testing suites.
API keys, OAuth tokens, or other authentication tokens may help to protect API endpoints, authenticate requests from trusted clients, and avoid misuse.
Track and prioritize security-related issues and concerns in a dedicated backlog to ensure timely resolution.
Now you know how to make your development process more secure. But what about the outcome of this process — the SaaS app itself? Let’s review measures that can make your application trusted and secure:
Implement strong authentication methods to verify the identity of users and prevent unauthorized access.
Assign roles and permissions based on users’ responsibilities and access needs.
It is important to maintain transparency in communication. Tell customers what types of data you collect, how you use it, and what third parties may access it.
Encrypt sensitive data using strong algorithms.
Create notification functionality to promptly notify administrators of suspicious activities, security incidents, or policy violations that require an immediate response.
Analyze app usage metrics and user behavior patterns to detect anomalies and potential security threats, such as account takeover attempts or unusual access patterns.
Conduct automated and manual security scans and assessments to identify and remediate software errors, vulnerabilities, and misconfigurations.
No matter how secure your SaaS application is, users’ behavior may pose a threat. This is how you can minimize risks from app usage:
Provide security awareness training so users learn to recognize and avoid common threats, such as phishing attacks and social engineering tactics.
Enforce password complexity requirements and encourage use of unique, strong passwords to protect accounts from unauthorized access.
Implement multi-factor authentication (MFA) to add an extra layer of security to user accounts and prevent unauthorized access.
By adopting the measures described above, you can avoid the majority of SaaS application security concerns. Most of the recommendations are general and apply to any software company that provides services to individual and corporate clients.
However, some edge cases can be detected only by a security specialist. Don’t hesitate to contact a reliable SaaS development services provider to optimize the security of your SaaS product. By analyzing your specific SaaS business, an engineering team may come up with more ideas to protect your app, users’ data, and the cloud environment.
SaaS product founders have to ensure their products meet the three principles of the CIA triad: data confidentiality, data integrity, and data availability.
These principles lay the foundation for all actions you can take to protect your SaaS product.
From the project kick-off meeting and launch of the project discovery phase, you and your engineering team should carefully develop an actionable plan to ensure impeccable SaaS security.
You can effectively mitigate SaaS security threats at three levels:
